Security Program Metrics
Security Program Development May 3, 2008 Comments Off on Security Program Metrics 57Metric Background
These statistics represent the information that has been collected through either our security development program tool or other survey based vehicles we use on the site. Enjoy!
Participant Demographics
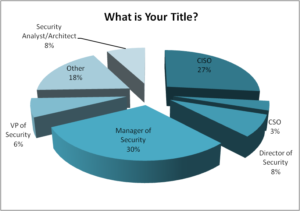
Q1. What is your title?
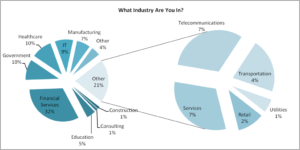
Q2. What industry are you in?
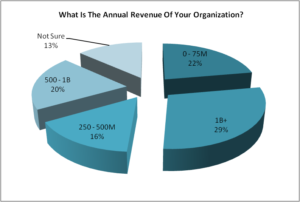
Q3. What is the annual revenue of your organization?
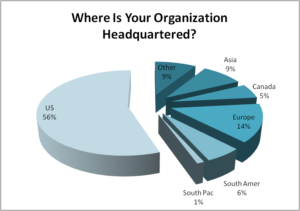
Q4. Where is your organization headquartered?
Mission and Mandate
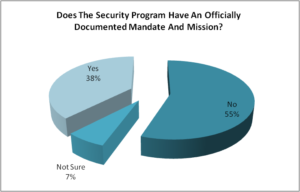
Q1. Does the security program have an officially documented mandate and mission?
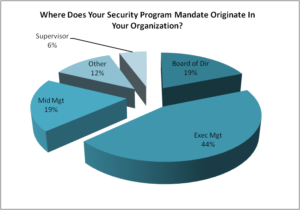
Q2. Where does your security program mandate originate in your organization?
Q3. Does your security program have a strategy for accomplishing its mission?
Roles and Responsibilities
Q1. Does the authority of the security office correlate to its level of responsibility?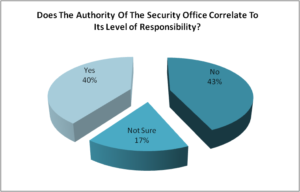
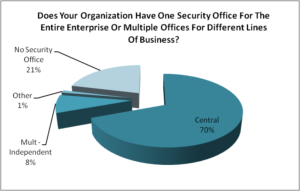
Q2. Does your organization have one security office for the entire enterprise or multiple offices for different lines of business?
Q3. Is your security program responsible for operational duties?
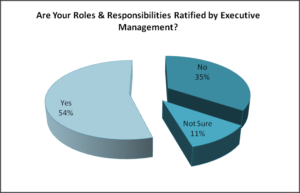
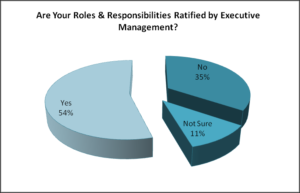
Q4. Are your roles and responsibilities ratified by executive management?
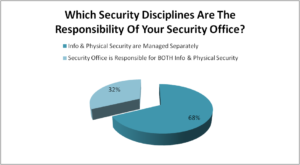
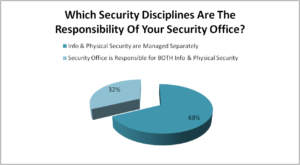
Q5. Which security disciplines are the responsibility of your security office?
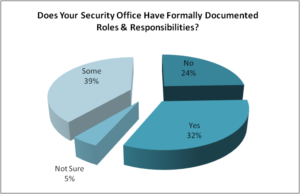
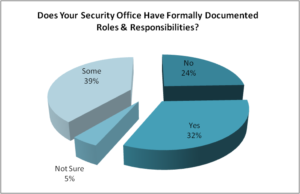
Q6. Does your security office have formally documented roles and responsibilities?
Security Policies
Q1. What is the state of your existing security policy?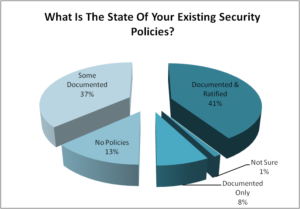
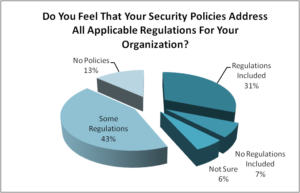
Q2. Do you feel that your security policies address all applicable regulations for your organization?
Q3. Do you feel that your security policies are specifically customized for your organization?
Q4. Do you feel that your security policies are comprehensive for the entire organization?
Q5. Does your enterprise environment meet or exceed the majority of standards and guidelines outlined in your security policies?
Q6. How often are your security policies reviewed and updated?
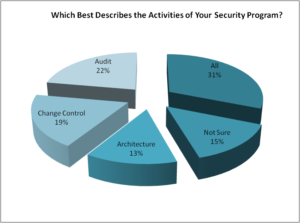
Q1. Which best describes the activities of your security program?
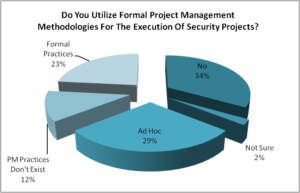
Q2. Do you utilize formal project management methodologies for the execution of security projects?
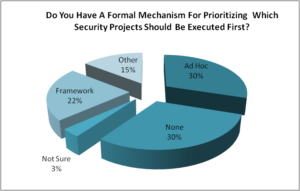
Q3. Do you have a formal mechanism for prioritizing wich security projects should be executed first?